Top 10 Emerging Threats for the Second Half of 2025
June 14, 2025 | by thecyberhub.net
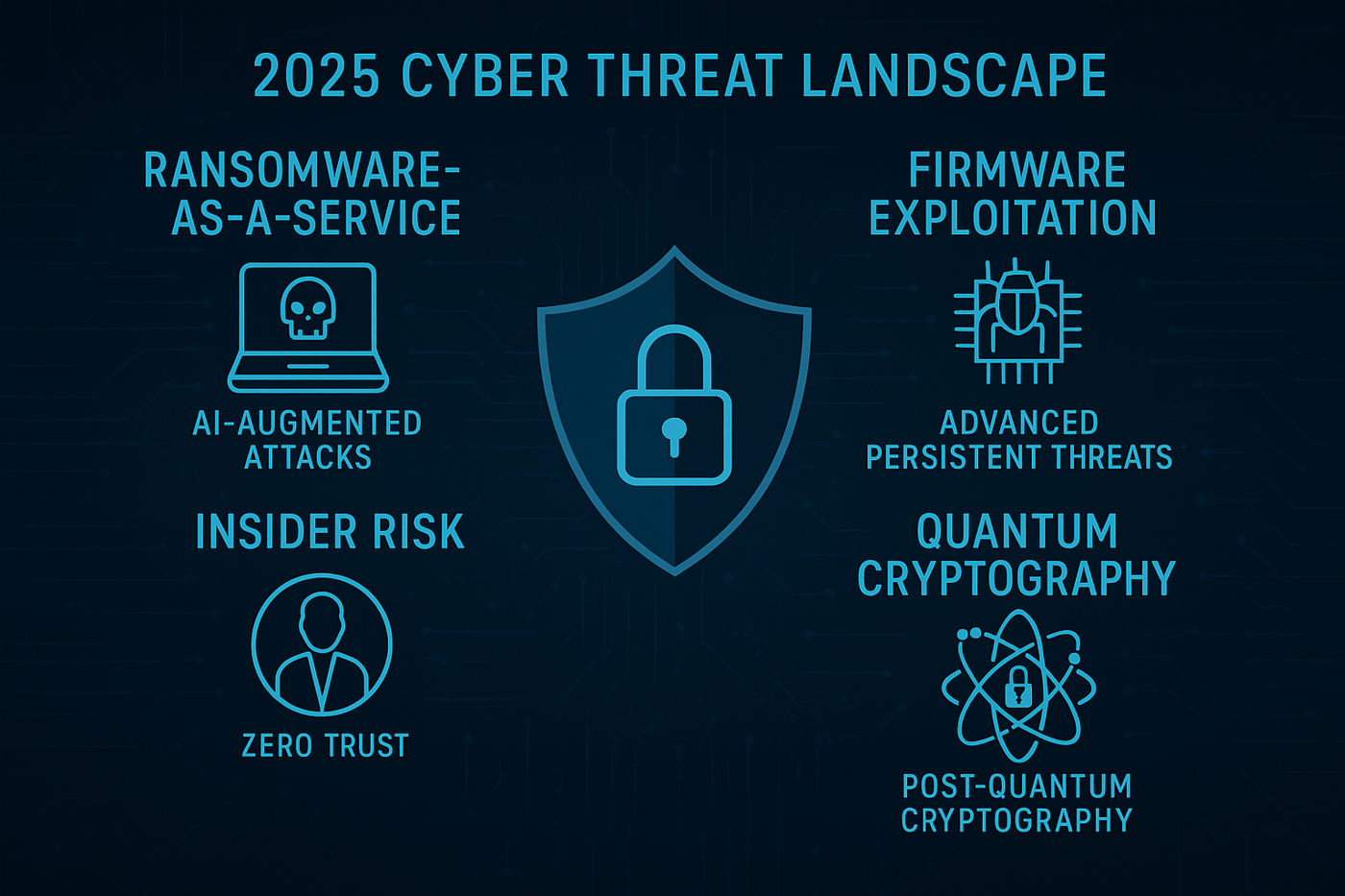
From ransomware-as-a-service (RaaS) and firmware exploitation to insider risk and the disruptive emergence of quantum cryptography, the 2025 cyber threat landscape is poised to escalate in complexity, sophistication, and asymmetry. Enterprises will confront hyper-automated, AI-augmented cyberattacks, polymorphic malware, and advanced persistent threats (APTs) targeting firmware and supply chain vulnerabilities. Simultaneously, the maturation of quantum computing introduces existential risks to classical encryption paradigms, necessitating accelerated research into post-quantum cryptographic algorithms, zero-trust architectures, and cryptographic agility to future-proof organizational resilience against evolving adversarial tactics.
1. AI-Powered Polymorphic Malware
Attackers are increasingly leveraging AI to create malware that can modify its code, behavior, and signatures dynamically, making it nearly undetectable by traditional antivirus and EDR solutions.
AI-powered polymorphic malware represents a significant evolution in cyber threats, leveraging artificial intelligence to create malware that can dynamically alter its code, behavior, and signatures. This adaptability makes it increasingly difficult for traditional security measures, such as antivirus software and Endpoint Detection and Response (EDR) systems, to detect and mitigate these threats.(sentinelone.com)
What Is AI-Powered Polymorphic Malware?
Polymorphic malware refers to malicious software that can change its code or appearance each time it infects a new system, thereby evading detection by signature-based security tools. When combined with AI, this malware can autonomously generate new variants, adapt its behavior based on the environment, and even mimic legitimate software to avoid detection.(impactmybiz.com)
Key characteristics include:
- Code Mutation: The malware alters its code with each execution, making it appear as a new, unique threat each time.
- Encryption and Obfuscation: It employs techniques like encryption and obfuscation to conceal its true intent and functionality.(paloaltonetworks.com)
- Adaptive Behavior: AI allows the malware to analyze its environment and adjust its actions accordingly, such as delaying malicious activity until security measures are less stringent.(impactmybiz.com)
- Evasion of Detection: By continuously changing its signature and behavior, AI-powered polymorphic malware can bypass traditional security defenses.
Real-World Examples
BlackMamba
A proof-of-concept malware named BlackMamba demonstrates the capabilities of AI-powered polymorphic malware. Developed using the ChatGPT API, BlackMamba generates a new keylogging payload each time it executes, making it nearly undetectable by EDR systems. It operates without a central command-and-control server, reducing its visibility and making traditional detection methods ineffective. (esecurityplanet.com, pmc.ncbi.nlm.nih.gov, medium.datadriveninvestor.com)
ChattyCat
Another example is ChattyCat, developed by CyberArk. This malware integrates ChatGPT directly into its code, allowing it to query for new modules and adapt its functionality in real-time. This approach enables the malware to evolve continuously and evade detection by traditional security tools. (pmc.ncbi.nlm.nih.gov)
Challenges for Traditional Security Measures
Traditional security tools often struggle to detect AI-powered polymorphic malware due to:
- Signature-Based Detection Limitations: Since the malware changes its signature with each execution, signature-based detection methods become ineffective.(portnox.com)
- Behavioral Analysis Challenges: While some EDR systems use behavioral analysis, the adaptive nature of AI-powered malware can mimic legitimate behavior, making it difficult to distinguish malicious actions from normal system operations.
- Lack of Centralized Control: The absence of a central command-and-control server in some AI-powered malware variants complicates detection and mitigation efforts.
Strategies for Defense
To combat AI-powered polymorphic malware, organizations should consider:
- Behavior-Based Detection: Implementing security solutions that focus on detecting unusual or malicious behavior rather than relying solely on known signatures.(identitysecurity.io)
- AI and Machine Learning Integration: Utilizing AI and machine learning algorithms to analyze vast amounts of data and identify patterns indicative of malicious activity.
- Regular Software Updates: Ensuring that all systems and applications are up-to-date with the latest security patches to minimize vulnerabilities.
- User Education and Awareness: Training users to recognize phishing attempts and other social engineering tactics that could lead to malware infections.(identitysecurity.io)
- Endpoint Detection and Response (EDR): Deploying advanced EDR solutions that provide real-time monitoring and response capabilities to detect and mitigate threats.
Further Reading
For more in-depth information on AI-powered polymorphic malware and strategies for defense, consider the following resources:
- Palo Alto Networks: The Dark Side of AI in Cybersecurity — AI-Generated Malware
- Arcserve: Researchers Use ChatGPT AI-Powered Malware to Evade Endpoint Detection and Response Filters
- SentinelOne: What is Polymorphic Malware? Examples & Challenges
- Identity Security: Defending Against Polymorphic Malware: AI’s Role in Cybersecurity
AI-powered polymorphic malware represents a significant challenge in the cybersecurity landscape. By understanding its characteristics and implementing advanced detection and defense strategies, organizations can better protect themselves against these evolving threats.
2. Quantum Decryption Pressure
While true quantum computing threats are still a few years away, state actors and advanced threat groups are allegedly stockpiling encrypted data for future decryption using quantum capabilities. The urgency to adopt quantum-resistant cryptography is growing.
The Real Threat: “Harvest Now, Decrypt Later”
While large-scale, fault-tolerant quantum computers are not yet operational, their potential to break widely-used encryption algorithms is already driving concern. One of the most alarming strategies attributed to state-sponsored actors and advanced persistent threat (APT) groups is the so-called “harvest now, decrypt later” tactic.
In this scenario, attackers exfiltrate encrypted data today — knowing they can’t decrypt it with current technology — and store it until a quantum computer becomes powerful enough to crack it. This deferred threat transforms seemingly secure communications and archives into future vulnerabilities.
Why This Matters Now
Most of today’s public-key cryptographic algorithms — such as RSA, DSA, and elliptic curve cryptography (ECC) — are fundamentally breakable by Shor’s algorithm on a sufficiently powerful quantum computer. This raises major red flags for:
- National security
- Intellectual property protection
- Healthcare and financial record confidentiality
- Long-term data retention in compliance-driven industries
The catch? Many of these sectors must retain sensitive data for years, even decades. So even if quantum computers remain years away from maturity, the data they target today may still be valuable — and exploitable — when quantum decryption becomes feasible.
The Push Toward Quantum-Resistant Cryptography
This looming danger is catalyzing the urgent transition to quantum-resistant cryptographic standards, also known as post-quantum cryptography (PQC). Governments and industry leaders are mobilizing:
- NIST’s Post-Quantum Cryptography Standardization Project is finalizing algorithms designed to withstand both classical and quantum attacks. The first standards are expected by 2024–2025.
- NSA and CISA are recommending federal agencies begin migration planning now.
- Tech vendors are developing hybrid cryptographic solutions that combine classical and quantum-safe algorithms to ensure a secure transition path.
What Organizations Should Be Doing Today
- Inventory Cryptographic Assets
Identify all systems that rely on public-key cryptography — especially those that handle sensitive, long-lived data. - Classify Data by Longevity and Sensitivity
Not all data needs quantum protection, but high-value data with long-term confidentiality requirements does. - Begin Migration Planning
Monitor the progress of NIST’s standards and engage with vendors offering PQC support or transition guidance. - Embrace Crypto-Agility
Implement systems that allow cryptographic components to be easily updated without redesigning the architecture. - Stay Informed
Quantum computing and cryptography are rapidly evolving fields. Organizations need to stay ahead of the curve to avoid becoming tomorrow’s breach headline.
Conclusion
The quantum decryption threat may feel theoretical today, but data harvested now could be exposed in the very near future. By proactively adopting quantum-resistant strategies, organizations can protect their critical assets from the inevitable arrival of quantum computing capabilities. The time to act is not when the threat materializes — it’s now, while we still have the advantage.
3. Supply Chain Manipulation 3.0
Beyond software supply chain attacks, hardware manipulation and firmware implants are becoming more sophisticated. Third-party vendors continue to be a significant attack vector.
In the age of hyperconnectivity, the supply chain isn’t just a logistical backbone—it’s a battlefield. And we’ve entered a new phase: Supply Chain Manipulation 3.0, where attackers don’t just breach systems—they rewrite trust at its source.
This isn’t about stealing data.
It’s about poisoning the pipeline.
What Is Supply Chain Manipulation 3.0?
Version 1.0 was simple: compromise a vendor, pivot into the target.
Version 2.0 evolved: inject malicious code into trusted software updates.
Version 3.0? It’s systemic. It’s strategic. It’s industrialized.
Attackers now target:
- Code repositories (GitHub, NPM, PyPI)
- CI/CD pipelines
- Firmware and hardware vendors
- Third-party APIs and SDKs
- Cloud service integrations
They don’t just breach—they embed. They don’t just exploit—they engineer dependencies.
Why It’s So Dangerous
Supply Chain Manipulation 3.0 weaponizes trust. It turns the very tools we rely on into Trojan horses.
- Invisible entry points: Attacks hide in build scripts, containers, or version updates.
- Delayed detonation: Payloads activate weeks or months later—after trust is established.
- Wide blast radius: One compromised library can infect thousands of downstream apps.
- Credential harvesting: CI/CD secrets, API keys, and tokens become collateral damage.
This isn’t just malware—it’s malware with a resume.
Real-World Examples
- SolarWinds: Attackers inserted malicious code into Orion updates, compromising thousands of organizations.
- CodeCov: A subtle tweak in a Bash uploader script exposed secrets from hundreds of CI/CD environments.
- Event-Stream (NPM): A popular Node.js package was hijacked and updated with credential-stealing code.
These weren’t brute-force attacks. They were surgical. They were patient. They were devastating.
How to Defend Against 3.0
Defense requires more than firewalls—it demands supply chain introspection:
- Software Bill of Materials (SBOM): Know every component, every dependency.
- Code signing and verification: Ensure integrity from source to deployment.
- CI/CD hardening: Rotate secrets, isolate environments, audit build steps.
- Dependency monitoring: Watch for sudden updates, ownership changes, or suspicious forks.
- Third-party risk scoring: Evaluate vendors not just on features—but on security posture.
What’s Next?
Supply Chain Manipulation 3.0 is just the beginning. Expect:
- AI-generated malicious commits
- Deepfake developer identities
- Compromised open-source governance
- Automated trust poisoning across cloud-native stacks
The battlefield is no longer your perimeter. It’s your pipeline.
Final Thought
Supply chains were built for speed, scale, and efficiency. But in the wrong hands, they become weapons of mass disruption. Supply Chain Manipulation 3.0 isn’t just a threat—it’s a paradigm shift.
We must stop treating dependencies as conveniences.
They are liabilities.
And they deserve scrutiny.
4. Ransomware-as-a-Service (RaaS) Industrialization
RaaS operations are evolving into highly organized, professional criminal enterprises offering customer support, revenue sharing, and subscription models, lowering the barrier for entry for novice attackers.
In the shadows of the digital economy, a parallel industry thrives—one that doesn’t sell innovation, but weaponizes it. Welcome to the industrialization of Ransomware-as-a-Service (RaaS), where cybercrime is no longer a rogue act of brilliance, but a scalable business model.
What Is RaaS?
Ransomware-as-a-Service is a subscription-based model where developers create ransomware kits and lease them to affiliates. These affiliates—often low-skilled attackers—use the tools to infect victims, while profits are split between the developer and the deployer.
It’s cybercrime franchised.
It’s malware with customer support.
It’s the gig economy gone rogue.
The Rise of Industrialized RaaS
RaaS has evolved from underground forums to full-fledged platforms with:
- User dashboards for campaign tracking
- Built-in encryption tools and payload generators
- Automated negotiation bots for ransom collection
- Affiliate vetting and tiered commission structures
- Marketing campaigns on dark web marketplaces
This isn’t just code—it’s infrastructure. And it’s growing.
Why It’s So Dangerous
The industrialization of RaaS lowers the barrier to entry. You no longer need to write malware—you just need a wallet and a motive.
- Scalability: One developer can empower hundreds of attackers.
- Anonymity: Cryptocurrency payments and Tor-based portals obscure identities.
- Specialization: Developers focus on evasion and payloads; affiliates focus on targeting.
- Resilience: If one affiliate is caught, the platform survives.
This modularity makes RaaS harder to dismantle than traditional ransomware groups.
Real-World Impact
From hospitals to municipalities, RaaS campaigns have crippled critical infrastructure:
- Conti and REvil operated like corporations—with HR, payroll, and internal memos.
- LockBit introduced bug bounties for its own ransomware platform.
- Black Basta and Hive used double extortion tactics—encrypting data and threatening public leaks.
These aren’t isolated attacks. They’re product launches.
What Defenders Must Do
Industrialized threats require industrial-grade defenses:
- Zero Trust Architecture: Assume breach, verify everything.
- Behavioral Analytics: Spot anomalies in user and system behavior.
- Threat Intelligence Feeds: Track RaaS platforms and affiliate chatter.
- Incident Response Playbooks: Prepare for encryption, extortion, and public fallout.
- Education & Simulation: Train teams with real-world ransomware scenarios.
The Future of RaaS
As AI and automation seep into every corner of tech, expect RaaS platforms to:
- Use AI-generated phishing emails
- Deploy adaptive payloads based on target environment
- Offer voice-based negotiation bots
- Integrate deepfake extortion tactics
The industrialization isn’t slowing—it’s evolving.
Final Thought
Ransomware-as-a-Service is no longer a threat—it’s a business model. And like any business, it thrives on efficiency, scale, and demand. The only way to fight industrialized cybercrime is with industrialized defense: transparent, adaptive, and relentless.
Let’s stop treating ransomware like malware.
It’s a market.
And it’s time we disrupt it.
5. Deepfake & Synthetic Media Attacks
Deepfakes are now being used for impersonation in executive fraud, social engineering, and disinformation campaigns. Advances in synthetic voice and video make it harder to verify authenticity.
6. Insider Threat Augmented by AI
AI tools are increasingly being weaponized by insiders to automate data exfiltration, bypass security controls, and escalate privileges without detection.
7. API Exploitation at Scale
As businesses continue rapid digital transformation, poorly secured APIs are becoming one of the most common and devastating attack surfaces.
8. Nation-State Targeting of Critical Infrastructure
Geopolitical tensions are fueling targeted attacks on power grids, water systems, healthcare, transportation, and financial institutions, often leveraging zero-days and living-off-the-land techniques.
9. LLM-Driven Phishing & Social Engineering
Generative AI models are enabling hyper-personalized phishing campaigns that convincingly mimic trusted contacts, making it significantly harder for users to discern fraudulent messages.
10. IoT Botnet Resurgence
With billions of poorly secured IoT devices online, botnet operators are retooling to launch massive DDoS attacks, disrupt critical services, and monetize device control.
RELATED POSTS
View all