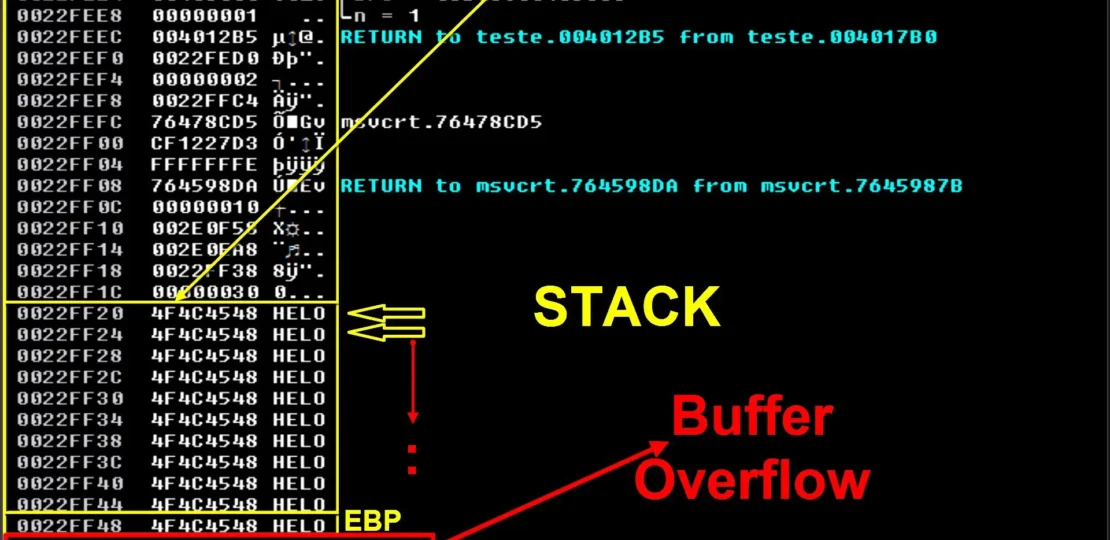
Buffer overflow is a type of software vulnerability that can occur when a program tries to store more data in a buffer than it can handle. This can lead to a situation where the excess data overwrites adjacent memory locations, potentially causing the program to behave in unexpected ways or even crash. Buffer overflows can also be exploited by attackers to execute malicious code, steal data, or gain control of a system.
Buffer overflow is a powerful technique that can be used to exploit software vulnerabilities and gain control of a system. It works by overflowing a buffer in memory with more data than it can handle, causing the excess data to overwrite adjacent memory locations. This can allow an attacker to execute arbitrary code or cause the program to behave in unexpected ways.
One example of a buffer overflow vulnerability is the Heartbleed bug, which affected the OpenSSL library used by many websites to secure communication. The bug allowed an attacker to read sensitive information from the memory of the affected server, including private keys, passwords, and other data. The vulnerability was caused by a buffer overflow in the implementation of the TLS heartbeat extension.
Another example of a buffer overflow vulnerability is the Wannacry ransomware attack, which affected hundreds of thousands of computers worldwide in 2017. The attack exploited a vulnerability in the Microsoft Windows operating system, which allowed the malware to spread through the network and encrypt files on the affected system. The vulnerability was caused by a buffer overflow in the implementation of the SMB protocol.
Buffer overflows can also occur in web applications, where they can be used to execute code on the server or steal sensitive data from the database. For example, the SQL Slammer worm, which affected many web servers in 2003, exploited a buffer overflow in the implementation of the Microsoft SQL Server.
Preventing buffer overflow vulnerabilities can be challenging, as it requires careful programming and testing to ensure that buffers are properly sized and checked for overflow. Some programming languages, such as Rust and Go, provide built-in protection against buffer overflow vulnerabilities by using safe memory management techniques.
Buffer overflow vulnerabilities can be a serious threat to software security, as they can be used to execute arbitrary code, steal data, or gain control of a system. While preventing buffer overflows can be challenging, it is important for software developers to be aware of the risks and take steps to mitigate them through careful programming and testing.
Buffer overflow is a vulnerability that occurs when a program or application tries to write more data to a buffer than it can hold. This vulnerability can be exploited by attackers to execute malicious code, modify data, or crash the program. In this article, we will discuss how buffer overflow can occur in Python and demonstrate an example.
In Python, the most common way buffer overflow occurs is when dealing with strings. In Python, strings are represented as arrays of characters. When a program reads data into a string, it reserves a specific amount of memory for that string. If the amount of data read is larger than the amount of memory reserved, a buffer overflow can occur.
Let’s take a look at an example of how buffer overflow can occur in Python:
“`
buffer = “A” * 50
input_data = input(“Enter your name: “)
print(“Hello ” + input_data + “, ” + buffer)
“`
In this code, we define a variable `buffer` that contains 50 characters. We then prompt the user to enter their name and store the input in the variable `input_data`. Finally, we print out a greeting along with the user’s name and the contents of the `buffer` variable.
However, if the user enters more than 50 characters, a buffer overflow can occur. The extra characters will be written beyond the end of the buffer, potentially overwriting other data in memory. This can result in unpredictable behavior, including crashes or the execution of malicious code.
To demonstrate this vulnerability, let’s run the code and enter a name longer than 50 characters:
“`
Enter your name: John Doe123456789012345678901234567890123456789012345678901
Hello John Doe123456789012345678901234567890123456789012345678901, AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
“`
As you can see, the extra characters in the name have been written beyond the end of the buffer, overwriting the contents of the `buffer` variable.
To prevent buffer overflow in Python, it is important to always ensure that the amount of data being written to a buffer does not exceed the size of the buffer. This can be done by checking the length of the input data before writing it to the buffer, or by using safer string handling functions such as `strncpy()` or `snprintf()` that automatically limit the amount of data written to a buffer.
In conclusion, buffer overflow is a serious vulnerability that can occur in Python when dealing with strings. By understanding how buffer overflow can occur and taking steps to prevent it, we can ensure the security and stability of our Python programs.
RELATED POSTS
View all